Guest post by: Sean Michael Kerner
Attackers are always looking for different ways to get users to click on malware. As presidential primary season looms in the U.S. Cisco Talos has been tracking an increase in politically-themed malware that is detailed in a new report.
The campaigns take different forms with some using the likeness of President Donald Trump as a lure to somehow incite users to an action they might not otherwise take, such as clicking on a link or opening a file with a macro.
"What is every single malware author trying to do? They're trying to get users to forget about best practices," Craig Williams, Director Talos Outreach at Cisco said. "They would love for users to kind of freak out in order to forget about best practices and then just start clicking on their malware."
Using Trump and Clinton As Lures
The campaigns tracked by Cisco Talos included malware that used both Trump as well has his 2016 Presidential rival Hillary Clinton as subject lines and topics. The key point for the attackers is to have a topic or figure that is controversial that the recipient may oppose very strongly and will trigger an emotional response. It is the emotional reaction that makes the politically themed malware successful, according to Williams, and it's also what helps it to spread around the internet.
The attacks tracked by Cisco Talos in its report are largely opportunistic, rather than being targeted. That is they are just being sent almost randomly to lists that attackers have gathered of email addresses. Though Williams noted that it's also possible that targeted attacks are occurring, though that wasn't the focus of the new report.
See also: How Tortoiseshell created a fake veteran hiring website to host malware
It's also important to realize that none of the attacks are making use of new or zero-day vulnerabilities. Rather, attackers are exploiting known issues or simply getting users to click through warning dialogue boxes.
The vast majority of these attacks are simply the user falling for tricks of the attacker and infecting themselves by clicking on enable macros, opening up an attachment or installing a program they shouldn't,
"The vast majority of these attacks are simply the user falling for tricks of the attacker and infecting themselves by clicking on enable macros, opening up an attachment or installing a program they shouldn't," Williams said. "That's why they're usually pairing fairly simplistic attacks with something that's going to be emotionally charged at the user, so that they don't really think through what they're doing."
Looking at Some of the Attacks
Among the samples detected are examples of ransomware and screen lockers that included images of Donald Trump. Not all of the samples actually worked and encrypted user data, though they still attempted to trick users into thinking data was lost.
RAT infected Word doc
Users have been regularly reminded that opening attachments from unknown sources isn't a good practise. One way that the politically themed malware is getting around that is with a topic that incites the user to click and then open the document or spreadsheet.
Cisco Talos found examples of the Konni remote access trojan (RAT) embedded executable in a Word document. There were also samples of spreadsheets that had embedded SWF (flash) files that included the ROKRAT malware.
One of the more innocuous politically themed items discovered by Cisco Talos is a tool called, Trump's Cyber Security Firewall. The report found that the goal of the Trump Firewall is actually to help harden Windows security in a politically motivated way.
While there was no obvious malware in the Trump Firewall samples found by Cisco Talos, Williams commented that it's not a good idea for anyone to download or use the tool.
"A general recommendation is to never install untrusted utilities," Williams said. "This is a type of utility that one version may actually be benevolent and may actually work as advertised, but it's very easily something that could be used to embed malware."
"Generally speaking, if you don't know who built it, and you don't know why they built it, you shouldn't be running it," he added.
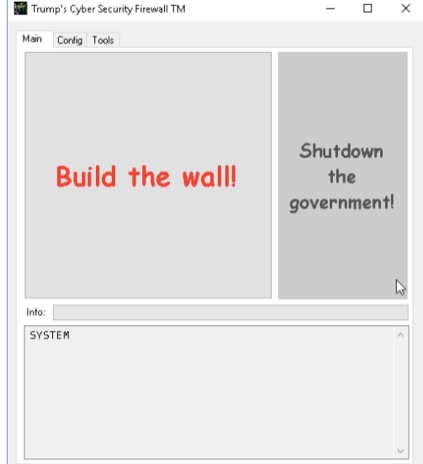
Sample screen from Trump cybersecurity firewall tool
Defending Against Politically Themed Malware
The Cisco Talos report lists multiple Indicators of Compromise (IOCs) as well as ways that Cisco technologies can detect the various threats that politically themed malware carry.
At a high-level though Williams provided some recommendations to help all users protect themselves and reduce risk. Fundamentally in his view, it really comes down to best practices.
Among the best practices outlined by Williams is to turn on automatic patching for applications and operating systems. Having some form of anti-spam system or service in place will also block many forms of opportunistic email attacks.
Finally, Williams suggests that users be careful what they click.
"If you get a super inflammatory email, realize it might be an attempt to manipulate you and it might make sense to not reply back," Williams aid. " You know, I think that's one of the skill sets that people need to learn as they use the internet is you don't have to reply to every email, you can disagree with a point of view, you can sit back and just delete it."
##
We welcome the re-use, republication, and distribution of "The Network" content. Please credit us with the following information: Used with the permission of http://thenetwork.cisco.com/.



